| subject | The Influence of Data Brokers on Consumer Privacy and Its Implications… | ||||||||||||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
관련링크본문
In an age where connectivity reigns supreme, the flow of information has become both a boon and a burden. Many individuals unknowingly partake in a complex web of interactions, where their details are often gathered, analyzed, and shared. It's a landscape that thrives on the exchange of bits and bytes, yet few pause to ponder the ramifications of this reality. What lies beneath the surface of this seemingly innocent sharing of knowledge? The consequences can be profound. As relationships develop between various entities, a tapestry of insights is woven around personal choices and behaviors. Information streams in from countless sources, painting a vivid portrait of preferences and habits. This phenomenon, while offering convenience and tailored experiences, also raises questions. Who holds the keys to this treasure trove of details? How secure are the pieces of ourselves that we inadvertently disclose? When we consider the intricate machinery operating behind the scenes, it becomes clear that many players are involved, and their motivations can vary widely. There’s often a fine line between beneficial use and intrusive monitoring, and this balance can tilt either way. In an environment where everything appears interconnected, the significance of maintaining control over one’s narrative becomes more vital than ever. The struggle to safeguard personal integrity is ongoing, and it demands attention from all corners of society. Ultimately, as individuals navigate the complexities of modern interaction, it is essential to remain vigilant. Recognizing the forces at play is the first step toward empowerment, allowing individuals to reclaim ownership of their own stories, lest they remain mere data points in someone else's grand analysis. The Role of Data Brokers ExplainedIn today's interconnected world, the handling of individual information has become a complex web. Many people are unaware of the intricate processes happening behind the scenes. The entities involved often operate quietly, yet their influence is profound. A wide range of personal details is collected and analyzed. This situation raises numerous issues that deserve attention. Navigating through the online landscape reveals a myriad of players. These organizations compile various types of content. They collect items such as shopping habits, online activities, and even social interactions. It may seem harmless, but the implications are significant. When information is aggregated, it transforms into a powerful tool that can be used in unexpected ways. One must consider the operational methods these entities employ. They exploit publicly available sources, alongside direct contributions from consumers. This mixture creates a holistic view of an individual. Moreover, sophisticated algorithms analyze this wealth of information to create detailed consumer profiles. These profiles ultimately guide marketing strategies and advertising practices.
Each of the aforementioned sources contributes to a vast pool of insights. Although individuals may not realize it, their online footprints are being meticulously tracked. The consequences can be far-reaching, affecting everything from targeted ads to personal recommendations. Consequently, understanding these operations is crucial for any individual concerned about their information and its management. The influence of these entities extends beyond simple marketing tactics. They play a pivotal role in shaping what consumers see online. By curating information, they can sway opinions and even affect purchasing decisions. Therefore, being informed about their operations is vital in an age where knowledge is power. Understanding Consumer Privacy ConcernsIn today's interconnected world, individuals often overlook the extent to which personal information is gathered and utilized. This reality prompts significant unease among many. The complexity of tracking, storing, and analyzing such information raises questions. Who has access to it? For what purpose? These inquiries underline the importance of comprehending how individual details are collected and used. Various entities engage in information acquisition, often without consumers' explicit consent. The methods employed to obtain these details can be both overt and subtle, and they frequently operate under the radar. For instance, online activities, social media interactions, and even everyday consumer choices contribute to a growing database of personal insights. Each click, each like, and each purchase adds a layer to the vast tapestry of an individual's identity. Consumers remain largely unaware of the specific channels through which their personal details are siphoned. Moreover, individuals may unknowingly disclose sensitive information in exchange for convenience. The allure of tailored experiences and personalized ads can be enticing. However, this often comes at a cost that isn't immediately apparent. Trust in companies handling such information is paramount. But how can one be sure that the information will not be misused or inadequately protected? Many are becoming more aware of their rights concerning information handling practices. Yet, understanding the nuances of what data is collected, who possesses it, and the legal implications can be a daunting task. The sheer volume of information flowing through various channels creates an environment where vigilance becomes essential. The need for greater transparency in these practices is evident, but often lacks implementation.
The landscape surrounding information collection is ever-changing and often obfuscated. As technology evolves, so too does the complexity of information acquisition. Consumers find themselves navigating a labyrinth of practices that may not always align with their best interests. Awareness is merely the first step; active engagement in understanding and controlling personal information is crucial for maintaining one's autonomy in a digital age. How Personal Information is Collected
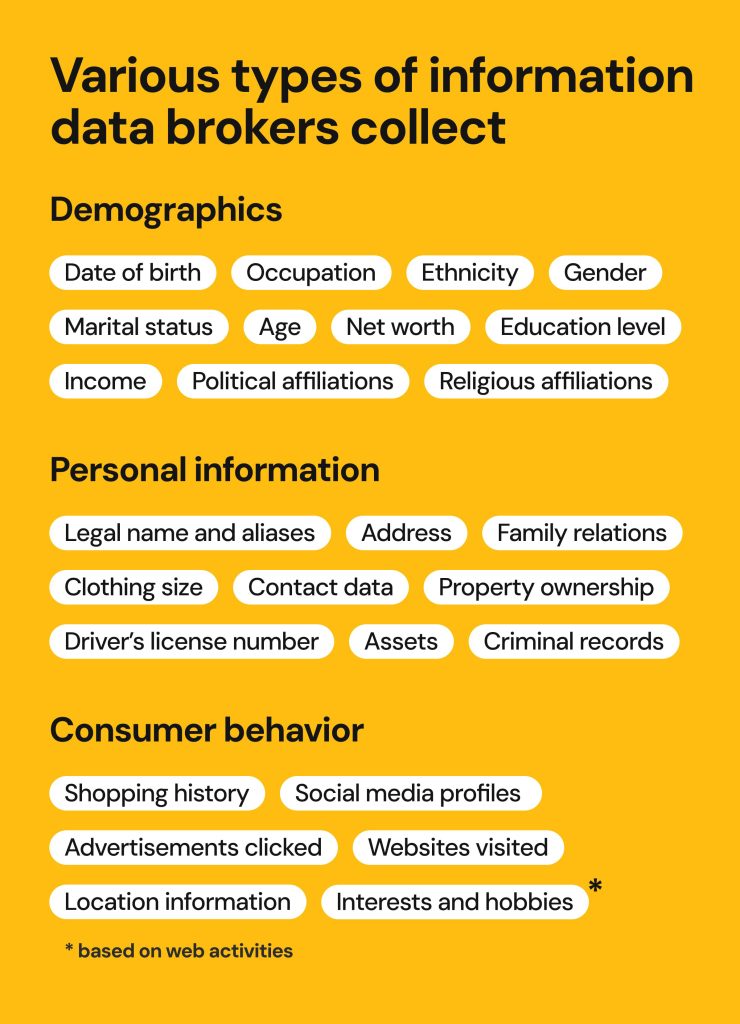
The collection of personal details is a complex process that involves various sources and methods. It begins with the digital footprints individuals leave behind. Every click, search, and interaction on the internet contributes to this growing pool of information. Many people are unaware of the extent to which their activities are monitored and recorded. From social media posts to online purchases, all actions can reveal valuable insights. Information is gathered through numerous channels. Websites employ cookies to track user behavior. These small files can collect data on browsing habits, preferences, and locations. Additionally, companies often utilize third-party applications that facilitate data acquisition. The widespread use of mobile devices further amplifies this collection process. Moreover, individuals often provide personal information willingly. This occurs during online registrations, surveys, or when signing up for newsletters. Each of these interactions presents an opportunity for firms to gather more data. In some cases, information is bought and sold among various entities, creating an expansive network of shared knowledge. Although many users might believe that they control their information, the reality is quite different. Furthermore, offline methods also play a crucial role in personal information collection. Retailers might collect details through loyalty programs or surveys conducted in stores. Events and promotions often require personal registrations, providing yet another avenue for data acquisition. Each of these methods adds another layer to the vast tapestry of personal profiles that organizations build over time. Ultimately, the combination of online and offline practices results in a comprehensive repository of details about individuals. This intricate system can lead to both beneficial and concerning outcomes, depending on how such information is utilized. As technology advances, the methods of collection will likely evolve, further intertwining personal lives with complex data ecosystems. The Business Model of Data Brokers
In today’s digital age, the monetization of personal information has become a lucrative enterprise. Companies thrive by harvesting insights from vast pools of consumer information, creating intricate profiles that marketers and advertisers find invaluable. The accessibility of such detailed profiles can reshape advertising strategies and elevate sales. Consumers often remain unaware of how their online behavior feeds this mechanism. These entities operate on a multifaceted business model. First, they gather vast amounts of information from numerous sources, ranging from social media interactions to public records. Next, they enrich this data by combining it with additional information from third parties. This enriched profile is then sold or shared with various stakeholders, opt out spokeo primarily businesses seeking targeted outreach. Many factors contribute to the profitability of this industry. The demand for precise targeting in advertising has surged, ensuring that personal information remains a hot commodity. Marketers crave specificity, whether for increasing efficiency in campaigns or maximizing return on investment. Such tailored approaches allow companies to communicate more effectively with potential customers.
Moreover, the ecosystem surrounding this trade is intricate. Transactions often involve various parties, including advertisers, marketers, and even researchers pursuing insights into consumer behavior. This interconnectedness raises questions about accountability and ethical considerations in the collection and dissemination of personal information. As the hunger for more precise targeting grows, so too does the potential for misuse. In essence, the business strategies employed here are driven by innovation and demand. The ongoing evolution of technology presents fresh opportunities for extracting insights from previously untapped resources. Organizations continue to refine their techniques to stay ahead in a competitive landscape, pushing the boundaries of what personal information can reveal. Legal Framework Surrounding Data SharingIn today's digital landscape, regulations play a crucial role in governing the sharing of information. Protecting individuals from unwanted exposure is paramount. Various laws and guidelines have emerged, each aiming to ensure transparency and accountability. Without these protections, the risk to personal information would be significantly higher. Legislation can vary greatly across regions. In some places, consumers enjoy robust rights regarding their own information.
Ensuring compliance with these regulations is essential not only for protecting individuals but also for fostering trust between businesses and consumers. Companies that fail to adhere to legal standards face significant penalties and reputational damage.
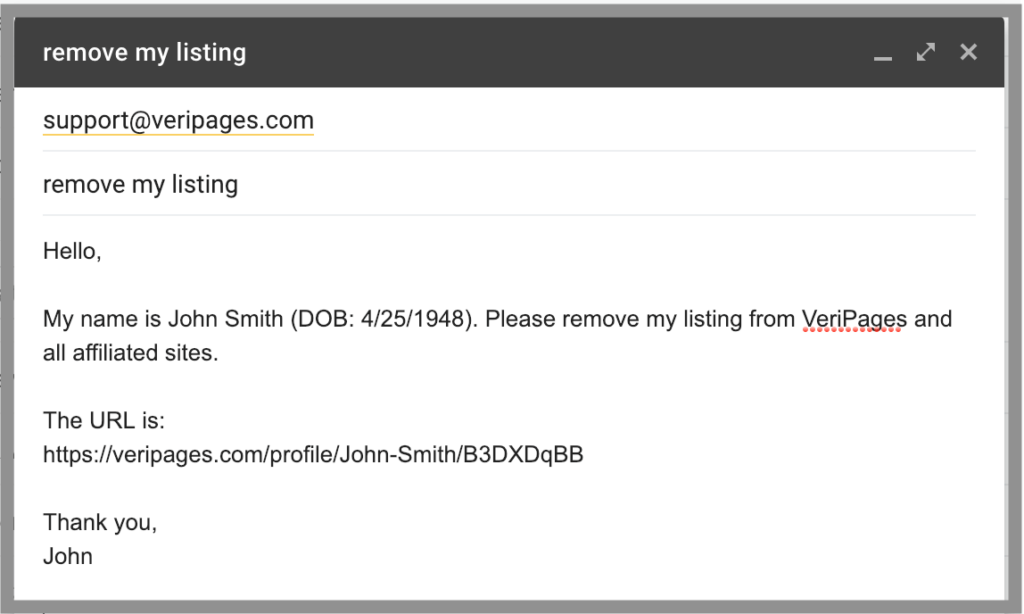
In recent years, lawmakers have started to recognize the importance of consumer rights. Movements advocating for stricter rules have gained momentum. As technology continues to evolve, the need for adaptive legal frameworks becomes ever more critical. This ensures that individuals maintain control over their information, thus reinforcing a culture of responsibility and respect in the digital ecosystem. Measures to Protect Your InformationIn today's digital world, securing personal information has become a pressing concern for many individuals. Numerous strategies exist to safeguard sensitive details from unauthorized access. It's essential to understand these protective measures to maintain control over one’s own information. Knowledge is power, and being informed can help prevent potential misuse. One common method is the use of strong, unique passwords for various accounts. Avoid reusing the same password across multiple platforms. Enabling two-factor authentication adds an extra layer of security. Regularly updating passwords can also reduce the risk of unauthorized access. Another effective approach involves scrutinizing the permissions granted to applications and websites. Often, users unknowingly allow excessive access to their information. It’s crucial to review the data shared with apps and carefully consider whether that level of access is necessary. Virtual Private Networks (VPNs) are useful tools as well. They encrypt your internet connection, making it harder for malicious entities to intercept information. A VPN serves as a shield, protecting your online activities from prying eyes. This additional layer of security is particularly beneficial when using public Wi-Fi networks. Education plays a vital role in this protective journey. Familiarizing oneself with potential threats and common scams can significantly enhance one's defense against identity theft. Additionally, employing monitoring services to alert individuals to unauthorized changes can be crucial. Investing in quality antivirus software is another indispensable measure. Such programs help detect and eliminate malware that may attempt to compromise devices. Regularly scanning devices ensures protection against evolving threats. These tools can be lifesavers in a world where cyber threats are increasingly sophisticated.
By employing these strategies, individuals can significantly enhance their security. Personal information is invaluable, and protecting it should be a priority. The digital landscape continues to evolve, but staying informed and proactive can make all the difference. Safeguarding one’s identity is not just a choice; it’s a necessity in our interconnected world. Measures to Protect Your DataIn today’s digital world, safeguarding personal information has become crucial. With the rise of technology, individuals face constant threats to their sensitive details. Therefore, understanding the steps to secure this information is essential. Each measure can significantly reduce risks. It’s not just about being cautious; it's about being proactive in defending against potential breaches. One effective way to enhance security is through the use of strong passwords. It's vital to create complex combinations that include uppercase letters, numbers, and symbols. Regularly updating these passwords adds an additional layer of protection. Additionally, enabling two-factor authentication can serve as a formidable barrier. This method requires a second form of verification, making unauthorized access much more difficult. Using reputable security software is another smart approach. Such tools can detect and neutralize threats before they compromise sensitive information. Always keep your software up to date to guard against new vulnerabilities. Using a virtual private network (VPN) can also shield your online activities. This allows you to browse the internet with added anonymity, protecting your movements from prying eyes. Awareness of phishing scams is vital. Always be skeptical of unsolicited emails or messages requesting personal details. Legitimate organizations rarely ask for sensitive information through these channels. Instead, navigate directly to their official websites for secure transactions. Taking the time to verify sources is essential for protecting your information. Reviewing privacy settings on social media accounts is also important. Many users unwittingly share too much information online. Adjusting these settings can limit access to personal data. Additionally, being mindful of what you post publicly can help prevent unauthorized collection of your information, ensuring that only intended parties view your shared content.
Consistent monitoring of personal accounts can also alert you to any unusual activity. Many services now offer notifications when suspicious actions are detected. Staying alert and informed helps mitigate risks significantly. In an era where threats are constantly evolving, knowledge and vigilance can serve as powerful allies. By implementing these strategies, individuals can take control of their personal information and prevent unauthorized access. Future Trends in Data PrivacyThe landscape of personal information protection is evolving rapidly. As technology advances, so do the methods employed to safeguard individual information. Increased awareness among individuals about their rights is changing the dialogue around information utilization. People are becoming actively engaged, paving the way for novel approaches to information governance. In recent years, the rising concerns regarding personal information security have led to the emergence of various strategies and solutions. Regulatory bodies are reacting to these concerns with new legislation aimed at enhancing protection measures. This shift hints at a future where individuals can exert more control over their information.
As individuals continually seek greater transparency regarding how their information is handled, organizations will be compelled to adopt more ethical practices. These shifts can lead to a fundamental rethinking of the relationship between companies and their clientele, where trust becomes central to the business model. Moreover, the technological advancements related to artificial intelligence and blockchain may introduce innovative solutions to reinforce individual rights. New tools and resources aimed at empowering individuals will emerge as a direct response to heightened demand for personal autonomy in information management. Alongside these innovations, social movements advocating for collective rights are gaining momentum. It is likely that organizations focusing on ethical data usage will differentiate themselves in a competitive market, attracting users who prioritize security and trust. Looking ahead, the emphasis will be on creating a balance between technological advancement and information integrity. Legislation will likely adapt to cover emerging technologies, ensuring that no one is left vulnerable as new systems are put in place. As societal norms evolve, so too will the expectations placed on organizations regarding how they handle sensitive information. In conclusion, the future promises both challenges and opportunities. With collective efforts from regulators, organizations, and individuals, a new standard for information protection is on the horizon. It will take time, but there is a visible shift towards a more secure and informed landscape. |
|||||||||||||||||||||||||||||||||||||||||||||||||
댓글목록
등록된 댓글이 없습니다.